What Is a Risk Assessment and Why Your Business Benefits
Information Security Risk Assessments

What Is a Risk Assessment and Why Do You Need One?
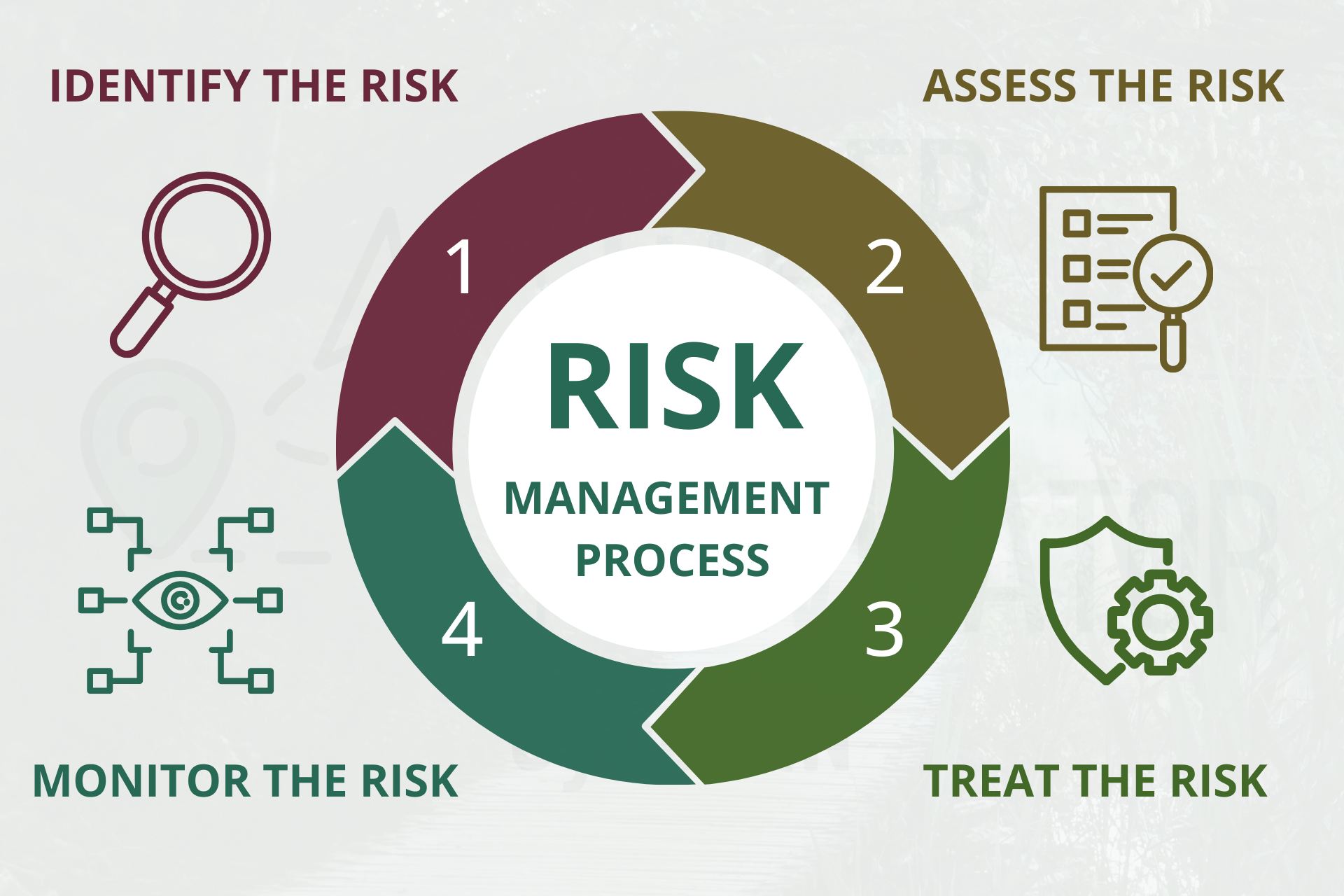
Ever wondered how businesses identify and reduce cybersecurity risks? That’s where risk assessments come in. A risk assessment is the process of analyzing potential threats, evaluating their likelihood and impact, and creating strategies to reduce those risks. It’s not just a technical exercise—it’s a roadmap for protecting your business.
In cybersecurity, there are different types of assessments, each with its own scope and purpose. A quick Google search can be overwhelming, and regulatory guidelines often add to the confusion. The best risk assessment evaluates your overall security maturity and forms the foundation of your information security program.
5 Types of Cybersecurity Assessments
Here’s a clear breakdown of the most common assessment types and what they mean for your business:
1. Information Security Program Risk Assessment
This is the most comprehensive type of assessment. It evaluates your security maturity across physical, administrative, and technical safeguards. Frameworks like ISO, NIST, and CIS provide robust standards that can be scaled to your business size and goals.
2. Vulnerability Assessment
These scans look for software and configuration weaknesses in your systems. They’re critical but limited in scope—they only cover one aspect of your security program. Many businesses mistakenly think this equals a full risk assessment.
3. Penetration Testing
Similar to vulnerability assessments, but with an added twist: testers actively try to exploit weaknesses. Useful for certain environments, but still limited and only reflects a point in time.
4. Third-Party Risk Assessment
Focuses on evaluating vendors and service providers. Important for supply chain security, but again, limited in scope.
5. Regulatory Assessment
Measures your program against specific compliance requirements, such as HIPAA or GLBA. These often cover only a subset of safeguards, not your entire security posture.
Why Risk Assessments Are Important
Risk assessments aren’t just a regulatory checkbox—they’re the backbone of your cybersecurity strategy. Here’s why they matter:
- Measure your current security posture
- Provide a roadmap to your desired maturity level
- Build trust with stakeholders
- Increase business resilience
- Reduce costs and improve compliance
Free Risk Assessment Tools
You can start with free resources to self-assess and track progress against industry standards. Check out frameworks from:
- Center for Internet Security (CIS)
- International Organization for Standards (ISO)
- National Institute of Standards and Technology (NIST)
Can I Conduct a Cybersecurity Risk Assessment Myself?
While free tools are helpful, a trained, objective third party ensures a thorough and unbiased assessment. Businesses don’t need the highest maturity level to reduce risk and meet compliance. An experienced professional can guide you toward the right safeguards and maturity level for your business.
Not Sure Where to Start?
If you’re unsure where your business stands or need guidance on the right assessment for your business, book a complimentary consultation with CyberRN. I’ll walk you through your options and help you take the next step toward stronger cybersecurity.