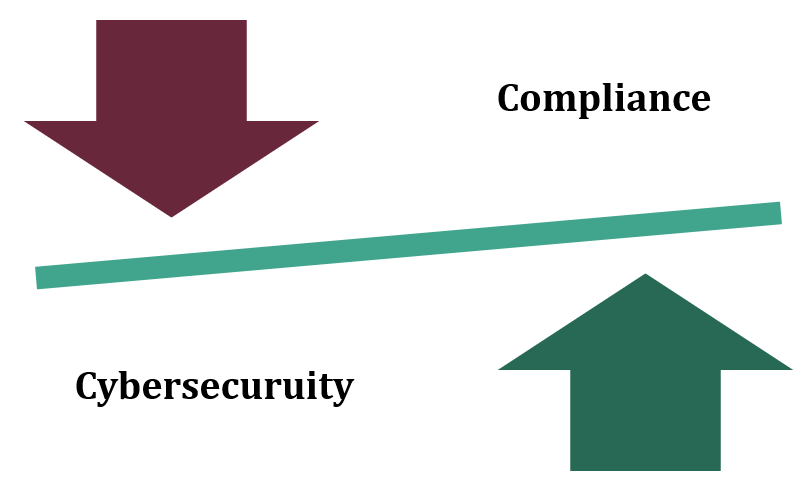
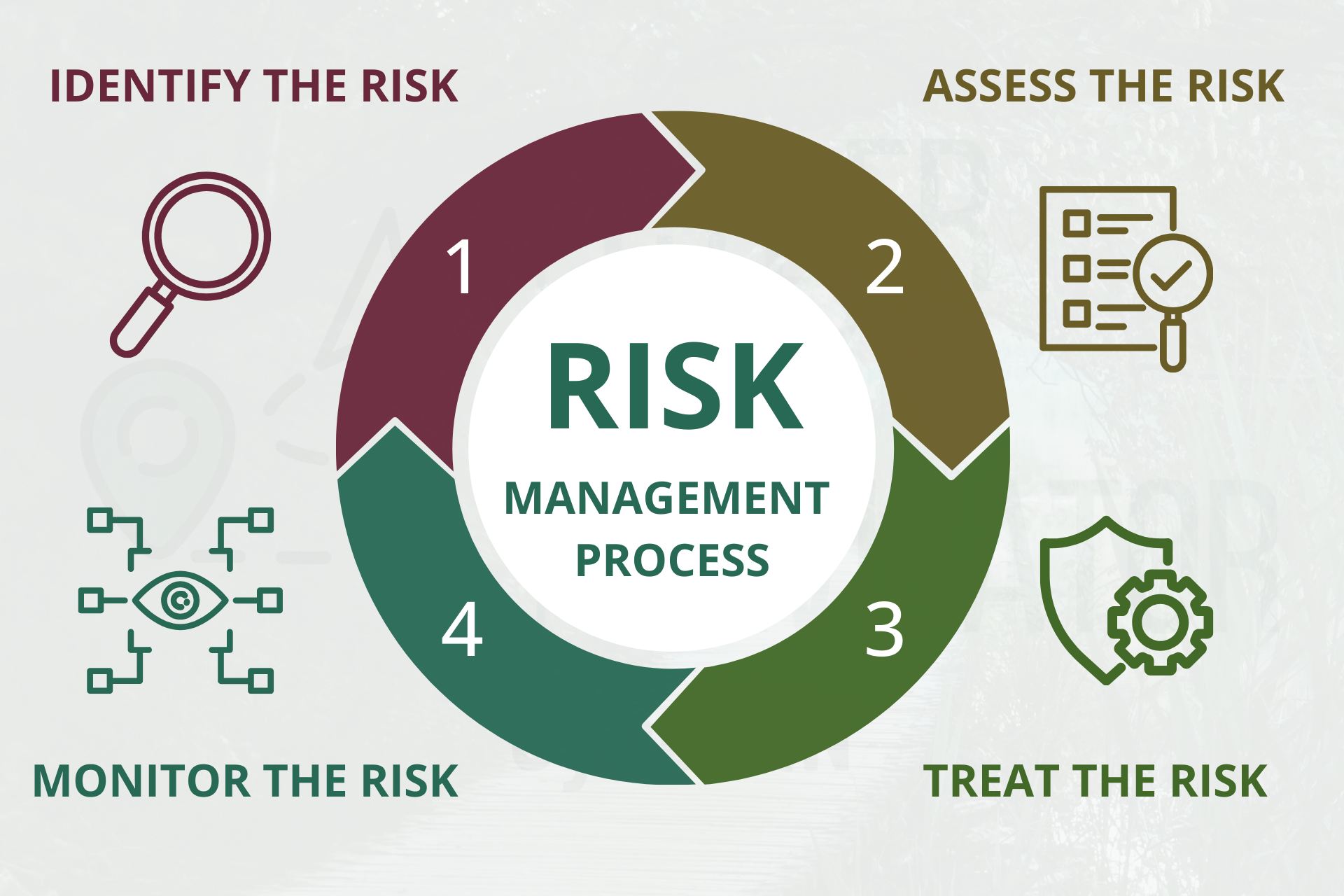
88% of Breaches Involve Human Error
Simple 3 Step Process to Reduce Human Error
Most incidents don’t start with “hacking” they start with busy people moving fast across email, chats, DM’s, calls and shared files.

Hate to say it 🫣
Most incidents don’t start with “hacking” they start with busy people moving fast across email, chats, DM’s, calls and shared files.
And the “obvious scam”? It’s not so obvious anymore as AI makes fake messages look and feel real.
Here’s a simple method: Pause ➡️ Review➡️ Act
If a message creates urgency or asks for money, access, logins, or an unexpected file/link…
That’s your
pause-and-review moment.
Want to know the psychology behind why people still fall for scams?
Stafford and Tessian studies show
88% of breaches involve human error.
Be Honest:
What’s a message or call you thought was real—but later realized it was a scam?
Drop it in the comments 👇
👉 Follow CyberRN for quick, actionable cybersecurity tips.